Getting new software has never been easier: one click and there you have a new project management app or lead qualification tool.
Yet more software isn’t always the merrier, especially when your employees take the liberty of installing them without any approvals or bypassing the IT department’s policies. Such actions are commonly known as shadow IT — and it’s a problem you can’t overlook.
What is Shadow IT?
Shadow IT is the practice of employees using unauthorized or unapproved software and hardware at the workplace. “Shadow” confers that the IT department doesn’t see the used technology and, therefore, cannot evaluate its security.
The presence of unsanctioned applications in the workplace is pervasive. In 2023, 41% of enterprise employees acquired, modified, or created technology outside of the IT department’s visibility, according to Gartner. A Capterra survey, in turn, found that 57% of small and medium-sized businesses (SMBs) struggle with shadow technology.
Examples of shadow IT can range from mostly harmless instances of an employee installing a new time-tracking app to more problematic cases of deploying a new database outside of the authorized cloud environments.
The problem in both cases is that the used solutions were not vetted for compliance and security and can therefore contain vulnerabilities. Likewise, unauthorized apps and application programming interfaces (APIs) can be used as an entry point for hackers or result in an accidental data breach. Cequence Security found that 68% of organizations have exposed shadow APIs, which pose security risks.
But Why Do People Use Shadow IT?
The common reasons why users opt for shadow IT are either the lack of suitable IT tools or long approval times for new software installations. In general, most people don’t understand the shadow IT security risks and see no harm in downloading “some app” on their devices. Likewise, many may be not aware of the equivalent authorized products available to them.
4 Shadow IT Risks Organizations Cannot Ignore
While the users’ intentions are usually pure — enhance personal productivity or access a more convenient technology — the consequences of shadow IT can be heavy: data breaches, compliance risks, cyber threats, and compatibility issues within the organization’s technology ecosystem.
Data Breaches
Sensitive business data may end up in unauthorized applications. If such an app gets hacked, your company will face collateral exposure. With the average cost of a data breach hovering at $4.45 million, that’s not something you’d want to risk.
Apart from targeted attacks, shadow technology can result in accidental data leakage. For example, when an employee accidentally sends a sensitive document via some messaging app to a personal contact.
Hacking and Exploits
Updates, patches, configurations, permissions, and critical security and regulatory controls are poorly understood by business users. But all these vulnerabilities are prime targets for hackers.
Outdated or unprotected shadow technology can be used for all sorts of cyber exploits — brute force attacks, malware injections, phishing, and so on. For instance, in 2022 over 5 billion malicious requests were set to unknown, unmanaged, and unprotected corporate APIs.
Shadow IT activities can also compromise the installed anti-virus software and intrusion detection systems, forcing your IT teams to investigate multiple alerts and the root cause issue instead of focusing on more meaningful work.
Compliance and Regulatory Risks
Unauthorized apps may not meet regulatory requirements around data privacy (e.g., GDPR) or industry security requirements (e.g., PCI-DSS). If such instances become known to the regulators, you’ll risk heavy penalties.
Shadow IT activities can also inadvertently cause IT infrastructure performance issues (e.g., a localized system failure), which could lead to breaches in customer SLAs. Again, that would require a lot of rehabilitation efforts.
Business Inefficiencies
Shadow technology may also pose interoperability issues, obstructing workflows that rely on shared computing assets or information. Since your IT team doesn’t plan for computing capacities, required by shadow technology, they may assign insufficient IT infrastructure to a given department — and subsequently struggle to understand how the resources are being used or what causes performance bottlenecks.
Shadow IT also drives up the operating costs. Duplicate licenses, increased data storage, and the proliferation of other cloud-based tools drive cost overruns. In fact, the average SMB spends over $43,500 annually on software it does not use regularly and 63% also admit that such apps have no impact or even drive a reduction of the company’s technology ROI.
How to Deal with Shadow IT: Best Practices
The challenge of shadow IT is that it’s hard to identify until it causes problems.
Organizations today operate large IT estates. The average company uses over 130 SaaS applications and multiple IaaS/PaaS solutions, not to mention on-premises resources.
Even with the most advanced IT asset management tools, finding unauthorized apps in such large environments is a needle in a haystack type of task. Likewise, many apps now double as personal and business ones. So merely banning access to Google Drive as a sweeping shadow IT policy change isn’t a solution as such measures can undermine legitimate business efforts. Instead of targeting edge cases, you should aim for wider transformations in your IT operations function.
To deal with shadow IT, you have to make IT so effective and responsive that end users have little reason to go their own way.
And here are the strategies we recommend for that.
1. Improve Asset Visibility
The average company has 30% more exposed assets than its asset management programs have identified.
The first task is to create a detailed asset inventory, documenting all elements within your tech stack such as:
- Local business apps
- SaaS products
- Virtual machines (VMs)
- Cloud and on-premises storage
- Integrated development environments
- Miscellaneous hosts and APIs
An asset management assessment serves the dual purpose of identifying unsanctioned apps on your network and consolidating IT spending. You’d likely end up surprised by the number of abandoned, redundant, and outdated products you’re still paying for.
Such an audit also helps you improve your cybersecurity posture. With a sweeping scan, you can identify:
- Outdated versions of software or firmware in use
- Designation and security status of various APIs
- Number of open ports for different systems
- Unknown hostnames and IP addresses
Then implement the necessary measures to tighten up your security and implement shadow IT monitoring measures.
Leverage different application mapping tools and network monitoring products to obtain visibility into all of your assets. Modern solutions cover all endpoints in on-premises, hybrid, and cloud environments.
2. Upgrade Your IT Service Management Practices
IT Service Management (ITSM) is concerned with the end-to-end delivery of IT services to end-users. Its core job is to ensure smooth infrastructure operations, timely provisioning of new resources, and service/help desk support.
Although ITSM is an important function, it’s frequently overlooked. Over 58% of ITSM practitioners, surveyed by Information Week in 2022, didn’t have an ITSM framework in place. Many also lacked self-service portals for users and effective IT service desk processes, which resulted in poor service levels.
Slow response times, rigid policies, and low quality of provided solutions by the ITSM function exasperate shadow IT. If your marketing team needs a new landing page ASAP, they cannot wait two weeks for their request for a new SaaS app to get approved. Instead, they’ll just go ahead with using an unsanctioned product.
Your goal is to align your IT department’s capabilities with the staff’s needs. And that starts with acknowledging shadow IT presence.
Instead of punishing users, explain the shadow IT meaning to them once again and then ask them to volunteer any information on such apps. Analyze the in-use software and bring the appropriate tools into the company’s security perimeter.
The next step is creating better workflows for requesting new software licenses, product features, or customizations. Set up a standardized request template for business users and lean approval workflow. Make a couple of people accountable for monitoring and responding to this stream.
Finally, create a company-wide app ownership structure, which assigns different software to teams/departments. Ensure that all employees understand which tools are already available to them and how these can be used in their work. Automate onboarding, data privileges sharing, and offboarding for users.
You can offload some of these processes to an IT operations partner such as Edvantis if you struggle to allocate resources internally. Our specialist can help set up effective processes for app lifecycle management, IT infrastructure monitoring, and tech support.
3. Empower Business Users with Low-Code Tools
“The prevalence of shadow IT has traditionally correlated to how much faster business units can get results by circumventing the CIO,” says Rex Booth, the CISO at identity vendor SailPoint.
Indeed, business users feel increasingly frustrated with legacy technologies that prevent them from getting their job done. So when they see a better app, they’ll go forward with using it without considering the shadow IT risks.
Low-code solutions can be a good alternative to haphazard app adoption and more complex software modernization projects.
Power Platform allows business users to create custom automation and even simple apps in the Microsoft ecosystem. With Power Automate, for example, business users can streamline a large number of CRM processes in Microsoft Dynamics. Power Apps, in turn, help build convenient products for HR, Sales, and Customer Support using visual tools and pre-made code components.
Providing users with access to low-code tools can reduce the itch to use unauthorized products.
4. Aim for Progressive Transformation
You can’t battle shadow IT in a day, especially when this practice was left unchecked for quite some time.
Instead, you should aim for a staged transformation, where you progressively improve your asset visibility, vulnerability management practices, and the levels of ITSM.
That’s the route Microsoft is taking to minimize shadow IT. Their vision spans beyond bringing unsanctioned solutions into the corporate perimeters, but also to enable teams to manage their own assets in line with Microsoft compliance standards.
To achieve this goal, Microsoft ranked the team’s current maturity and designed a roadmap for the laggers to move up to the optimal standards.
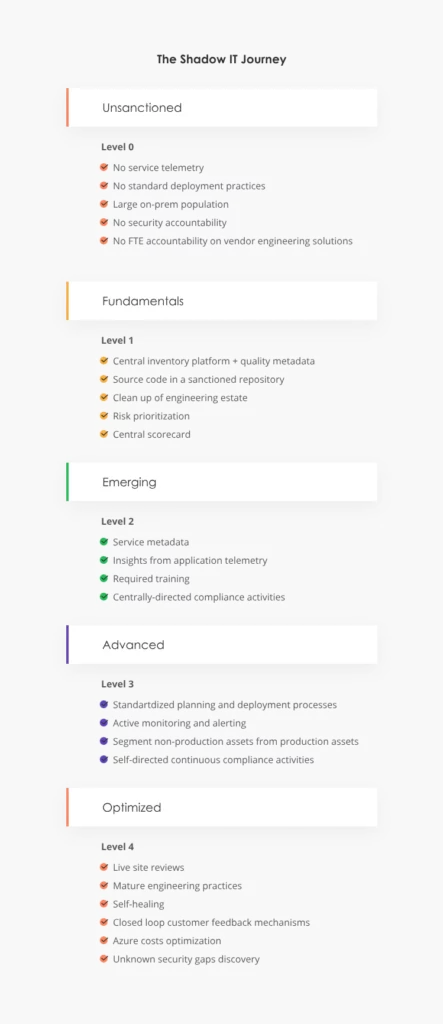
Source: Microsoft
Other leaders can take a similar approach: implement fundamentals first around security accountability, software provisioning practices, and ongoing solution maintenance. Then move on to more advanced measures.
To achieve the most impact, all the technology- and process-level improvements at the IT side should be combined with proactive employee outreach, as well as training on security risks.
Conclusions
Shadow IT proliferates because your processes cannot keep up with the end-users’ demands. Poor IT governance processes, lengthy technology provisioning lifecycles, and lack of awareness of cybersecurity further exacerbate the issue.
Mitigation of shadow IT often requires a set of improvements in ITSM and operational governance, rather than one-off “patching”. Edvantis would be delighted to advise you on different strategies for strengthening your IT function and minimizing the risks and impacts of shadow IT. Contact us!
FAQs About Shadow IT
Shadow IT is rarely a good occurrence as it’s a symptom of wider problems in your organization: low ITSM maturity, aging software, and suboptimal purchase cycles for new technology. When your people are forced to circumnavigate the official policies to get the required tools, your IT function needs an overhaul.
The common negatives of shadow IT include increased chances of data breaches, cyber attacks, or data loss. In addition, shadow IT increases operational spending and can affect the performance levels of authorized infrastructure.
A shadow IT is a set of procedures and protocols for the adoption, approval, and management of new technology within a company. Its main goal is to formalize the process of obtaining authorization for new software and hardware and bring it in line with the company’s security and compliance requirements.
Embracing shadow IT means progressively transferring the unsanctioned assets into the corporate security perimeter. The process assumes having an open conversation with your staff about the software they’re using and reaching an agreement on how these tools can be included in the corporate list of products or replaced with existing solutions.


